Although IT teams and MSPs continue to ramp up their security efforts, ransomware attacks show no signs of slowing down. Statistica’s ransomware report shows that in 2022, there were approximately 493.3 million ransomware attacks, and while this is a decrease from the 625.3 million attacks that occurred in 2021, it’s still higher than all the other years in the last decade.
So why have ransomware attacks been increasing in recent years, and what makes them so effective? To truly understand the origins of recent attacks, we need to look back at 2019, a year that brought forth all kinds of new cyberattacks that no one had ever seen. This post will go over the ransomware attacks of 2019 before diving into the ransomware statistics of today’s world and how to better protect your business.
How did ransomware evolve?
At the center of ransomware’s evolution in 2019 was a major shift away from high-volume, low-return campaigns (think mass spam and exploit kit campaigns) in favor of low-volume, high-return attacks specifically targeting businesses and organizations that a) have the funds/insurance coverage necessary to pay large ransom demands; and b) are especially sensitive to downtime (and therefore more likely to pay).
The security company CrowdStrike dubbed this approach “big game hunting” and it’s a model being proliferated by two of the largest and most lucrative ransomware operations currently active.
Cybercrime organizations that use ransomware: Sodinokibi (REvil) and Ryuk
The chart above tracks the shifting “market share” of the most active ransomware operations based on infections reported to ransomware incident response specialists Coveware.
It’s a clear illustration of the rise of Ryuk and Sodinokibi (also referred to as REvil). Together, those two operations accounted for half of the infections Coveware saw in Q4 2019. Although these two groups rose to fame in 2019, they are still two of the most prominent ransomware organizations in the world today. Ryuk attacks around 20 organizations per day, and 1 in 3 ransomware attacks involve REvil. Revil was officially dismantled in January of 2021, but then reappeared later in the year and continues to exist to this day.
Whereas Dharma, Phobos, and other operations cater to lowest-common-denominator cyber criminals looking for ransomware they can easily deploy and be as hands-off with as possible, the criminals behind Ryuk and Sodinokibi are a more exclusive group. They don’t license their ransomware out to just anyone, and they take a more manual approach that requires more expertise. Rather than simply drop an executable and run, these attackers make sure the stage is set for a more significant impact by leveraging reconnaissance, privilege escalation, and lateral movement techniques to entrench themselves throughout victim networks first. In addition, they also take the time to disable security tools and backups, only then executing the ransomware to devastating effect.
Ransomware statistics for 2019
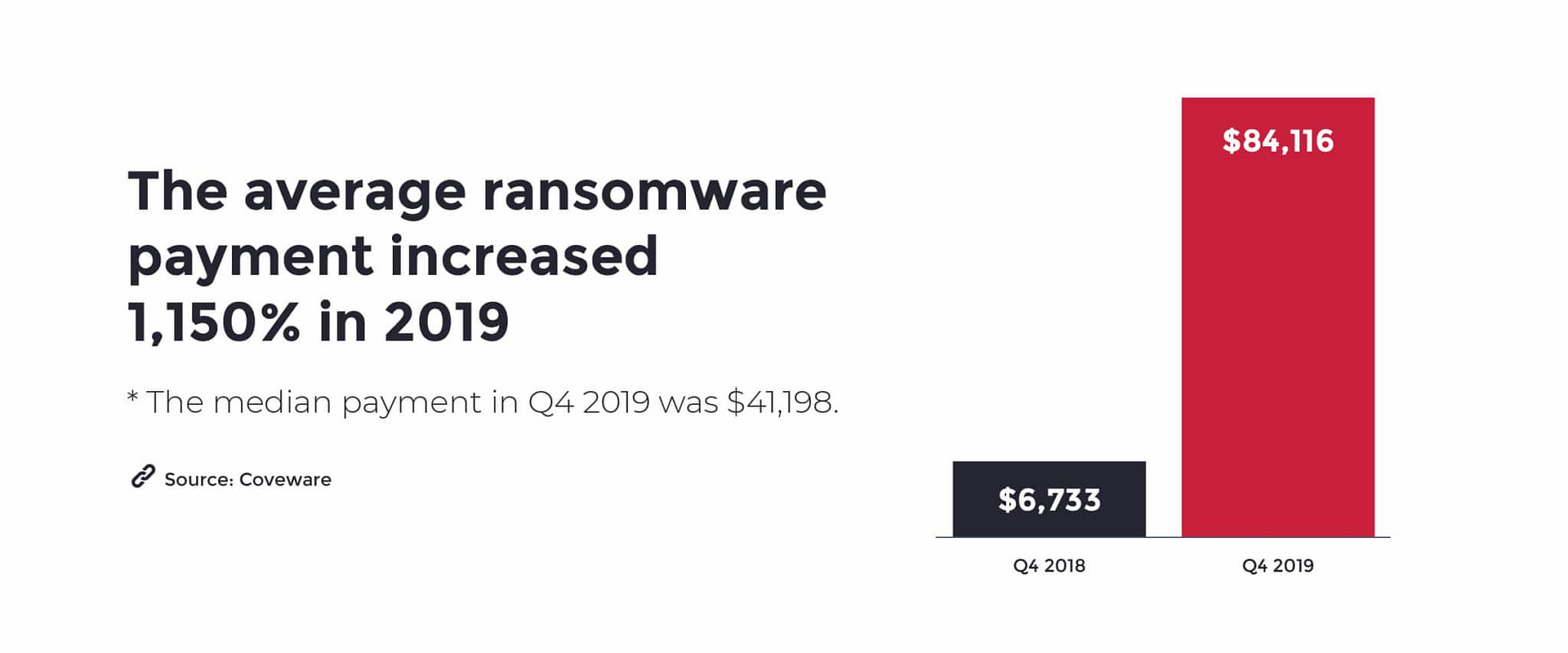
$84,116 paid for ransomware in 2019. According to Coveware, that’s not the average amount demanded in Q4 2019. That’s the average amount paid. Up from an average of $6,733 just 12 months prior.
That figure is heavily skewed by Ryuk and Sodinokibi (the median payment in Q4 2019 was $41,198). Demands from both of those actors can typically reach six or even seven figures, making even just a single successful attack potentially extremely lucrative.
Cases in point:
- Ryuk attackers extorted over $1 million in ransom from two Florida cities in just one week.
- A single Sodinokibi affiliate appeared to snag $28customer-count in three days.
The amount of money being funneled back to these criminals to fund future attacks is deeply troubling, and the size and quantity of ransoms being paid is even causing insurance providers to raise their cyber-insurance rates as much as 25%.
Why are attackers so successful at convincing organizations to pay? The primary answer is downtime.
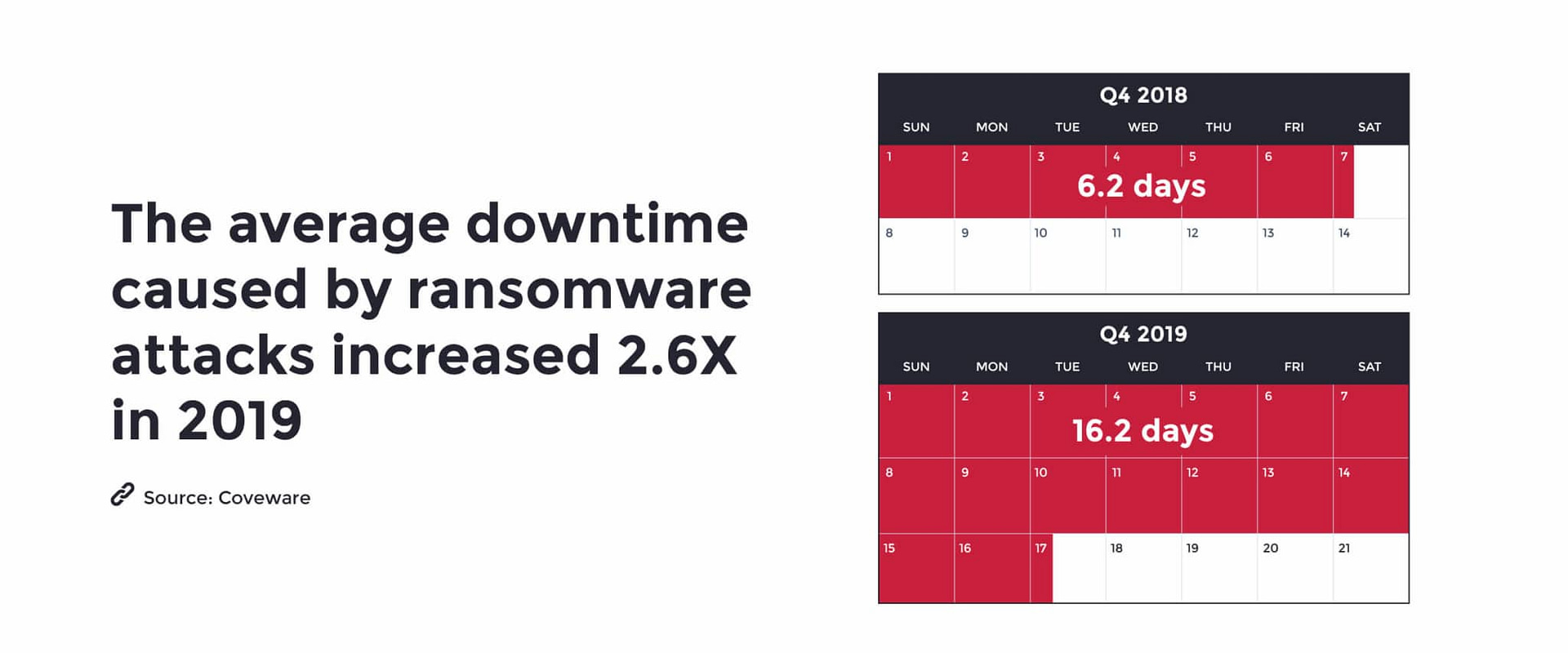
Beyond the jaw-dropping increase in ransom amounts, another extremely significant number pertaining to current ransomware attacks is 16.2 — that’s the average number of days companies are experiencing infection-related downtime (again, according to Coveware).
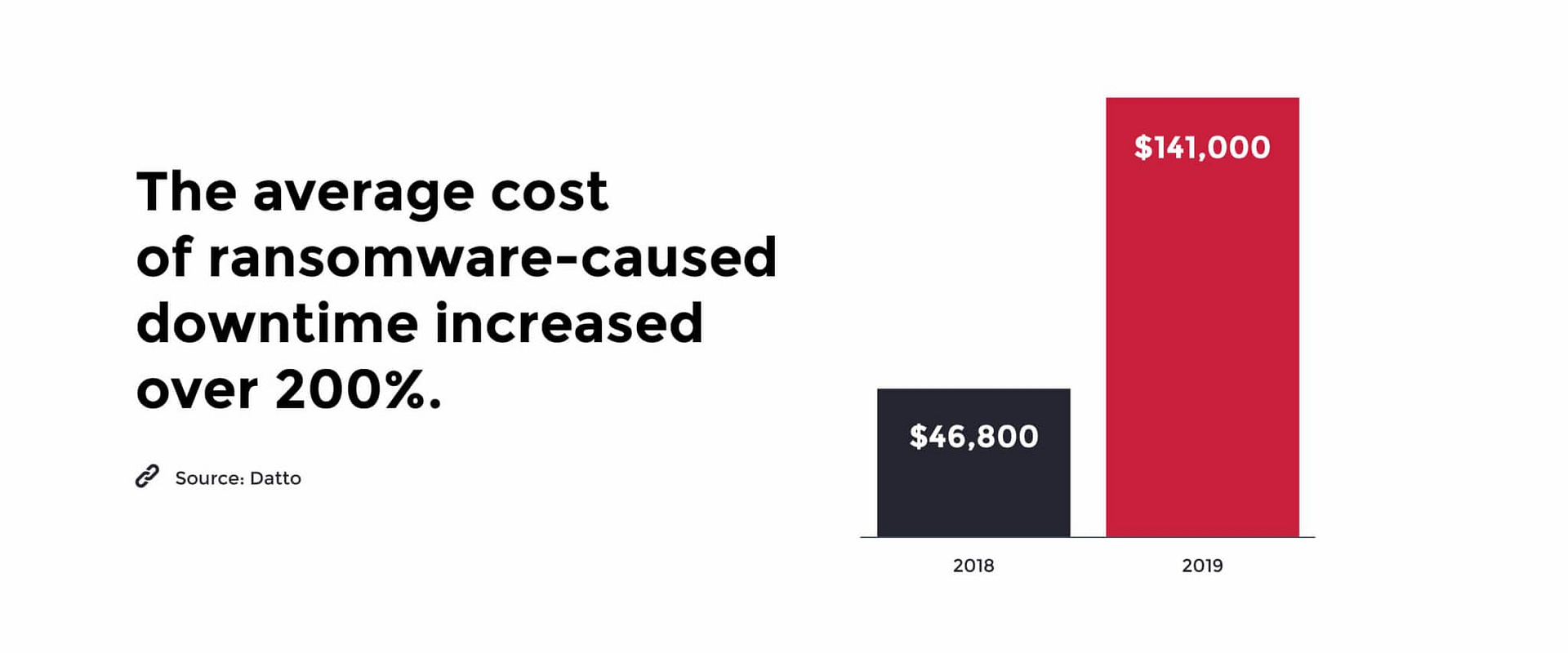
It’s no surprise, then, that the costs associated with ransomware-related downtime are also going up.
These figures are sobering. How many businesses (especially SMBs) can afford to lose $140,000, and experience more than two weeks of downtime and disruption?
They’re also prompting organizations (and their insurance providers) to consider all options, especially when working backups aren’t available. Even when working backups are available, however, there have been cases where organizations have determined that paying the ransom and taking a chance with decryption keys is potentially less costly than the time and effort it would take to restore their systems on their own.
Ransomware statistics for 2023
Now that we’ve gone over some of the ransomware attacks of the past, let’s see what the ransomware statistics are for 2023.
- This year, Chainanalysis predicts that organizations will pay $898.6 million in ransomware before the end of 2023. Every day, that number is inching closer to 2021’s $939.9 million that was paid for ransomware attacks. This alarming statistic shows that not only are the number of ransomware attacks increasing, but the cost and damage they inflict on businesses is increasing as well.
- According to Zscalar, “Ransomware attacks increased by over 37% in 2023, with the average enterprise ransom payment exceeding $100,000 with a $5.3 million average demand.” Even for enterprises, $5.3 million is a significant amount of money that is better used for other purposes, such as supporting business growth, rather than fending off threats and cybercriminals. Unfortunately, even though $5.3 million is an insanely high number for a demand, many companies meet the demands of cybercriminals to protect their business from further damage or destruction.
- There are 1.7 million ransomware attacks every day, which means there are 19 ransomware attacks occurring every second. This just goes to show that cybercriminals have no intention of easing up on their attacks, so IT teams should never ease up on their security efforts. It’s true that 1.7 million attacks per day is an astronomical number, but as long as businesses are aware of the threat and follow cybersecurity best practices, they will be well-prepared for whatever comes their way.
- For 2023, the average cost of a ransomware attack is $1.85 million, an insanely high number for most businesses. The main reason why companies shut down after a ransomware attack is that they are unable to recover financially, especially small businesses or MSPs. Additionally, this number continues to rise every year, which means it’s more important now than ever before that IT teams protect themselves from cybercrime.
Unfortunately, this list of ransomware statistics can go on and on, but one trend is clear: ransomware is still very much a threat today as it was in 2019, and the threat is increasing on many fronts. Since the number of ransomware attacks is rising, along with the cost for businesses, IT teams need to make security a top priority to protect themselves from this ever-growing threat.
Which businesses are targeted by ransomware?
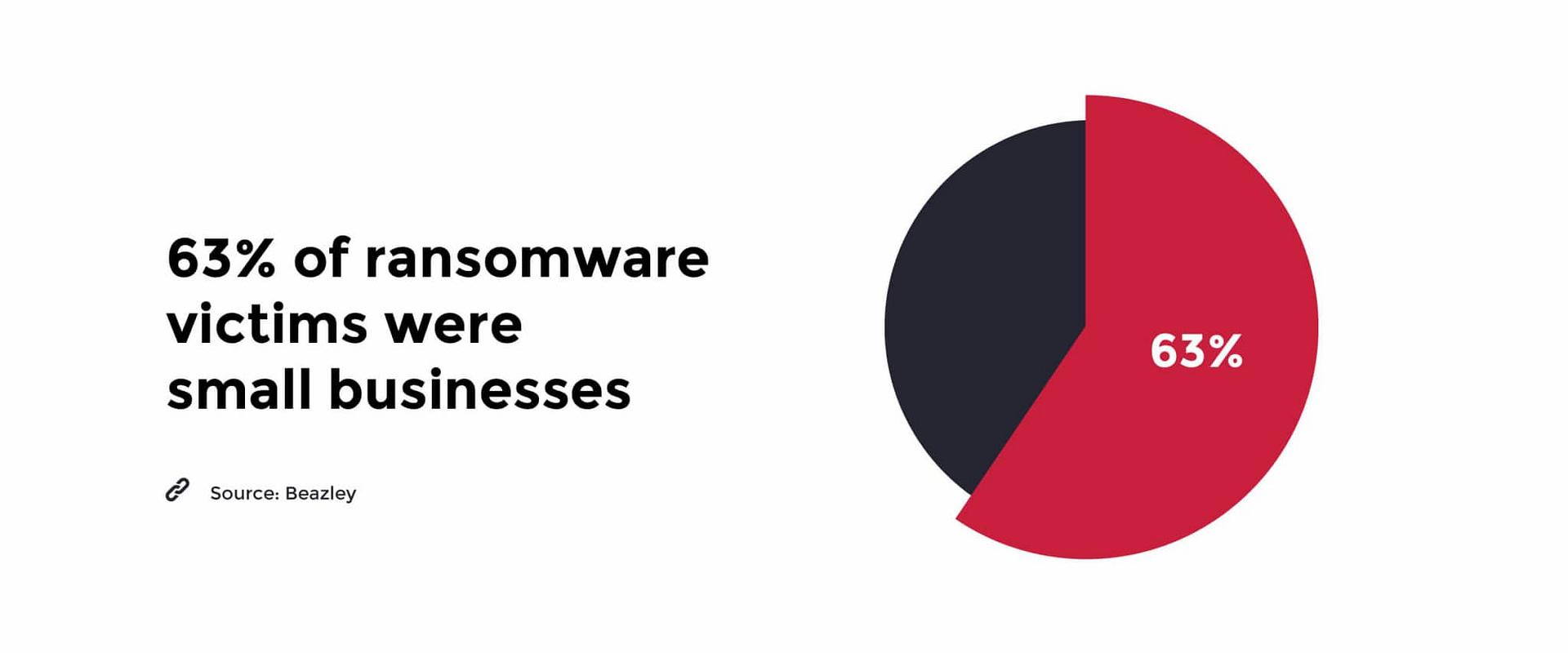
While attacks on large organizations like Travelex and municipalities dominate the headlines, the truth is nearly two-thirds of ransomware victims in 2019 were small- and medium-sized businesses, who are obviously less well-defended and prepared to successfully manage an active infection.
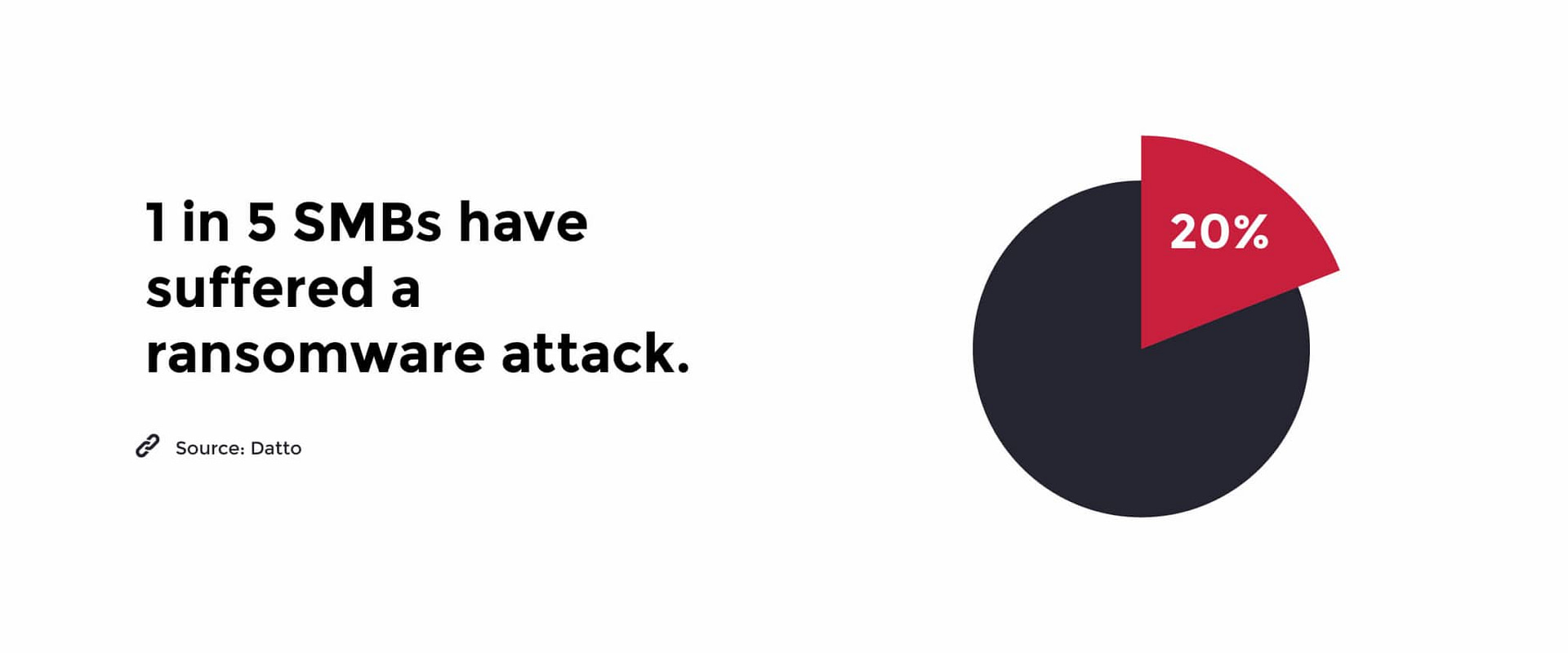
For SMBs, it truly is a matter of not “if” but “when,” with 20% of them reporting they’ve already experienced an attack.
In addition to SMBs and enterprises, municipalities, healthcare providers, and schools were extensively targeted in 2019, specifically due to their reputation for having outdated/vulnerable systems, a low tolerance for downtime, and a demonstrated willingness to pay ransoms.
Learn how our customer, H.E.R.O.S., was able to quickly bounce back from a ransomware attack with minimal downtime and lasting damage.
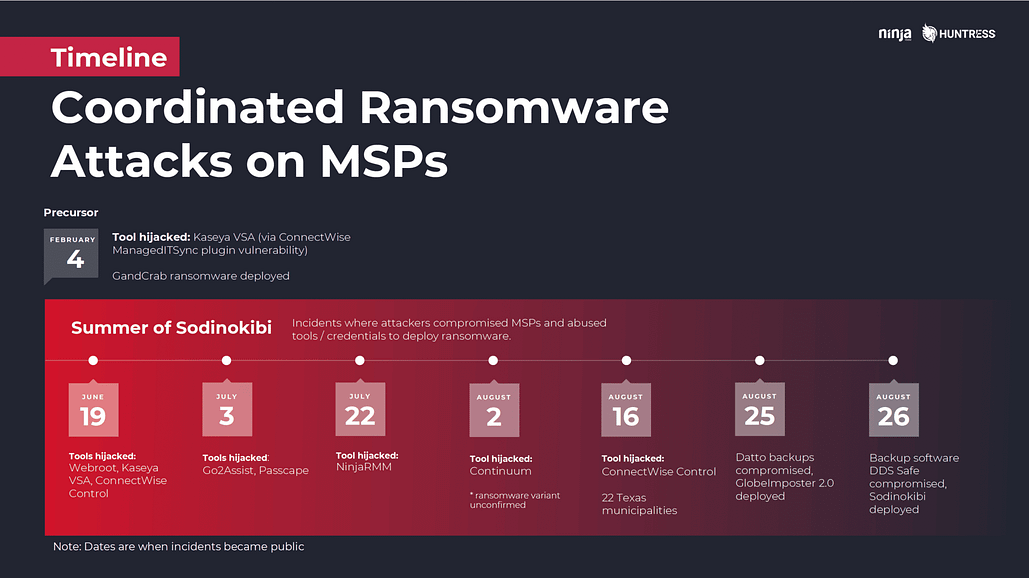
An especially concerning trend for those of us in the MSP space is the spike in attacks specifically targeting managed services providers. According to insurance provider Beazley, one quarter of the ransomware incidents reported to them in Q3 2019 were found to have originated with an attack on their IT or managed services provider.
We covered the trend in detail in our webinar with Huntress Labs, “How MSPs Can Survive a Coordinated Ransomware Attack” and responded with our own security initiatives, including making two-factor authentication (2FA) mandatory for using NinjaOne.
Initially, the trend was primarily driven by Sodinokibi actors, but by the end of the summer other actors had seen the opportunity and were getting in on the act.
The allure of compromising MSPs is obvious — doing so potentially gives attackers access to their powerful remote management tools and by extension, all of their clients. The MSP community is fighting back, however. MSPs and vendors across the space are proactively stepping up their game, calling for increased security from their peers, and are coming together to share vital threat intel.
What can you as a provider or customer of an MSP do your part and protect yourself?
How IT teams and MSPs can prevent ransomware attacks
The good news is that, despite the growing maturity and sophistication of ransomware operations, the vast majority of attacks are preventable by doing five things:
- Secure RDP: Don’t expose it to the Internet! Lock it down (how-to here).
- Disable Office macros (when feasible): Same goes for OLE and DDE (here’s how)
- Enable MFA on everything: This helps prevent account takeovers and tool hijacking.
- Invest in email and DNS filtering: The goal is to protect end users by stripping out as much of the bad stuff as possible before it reaches them.
- Invest in patch management: Automate things as much as possible with a solution that can apply both Windows and third-party updates. This report shows that 57% of data breaches are attributed to poor patch management.
And of course, utilize a properly configured backup solution — and actually test recovering from backups at scale. Having multiple restore points and offsite replication is key. Remember Shrodinger’s Backup: “The condition of any backup is unknown until a restore is attempted.”
This is just the tip of the iceberg as far as defensive activities are involved, but with the vast majority of ransomware being delivered by RDP compromise and emails (typically with malicious Office documents attached), doing even just these five things will drastically reduce your risk.
It also helps to have an RMM and IT management solution, such as NinjaOne, that allows you to set the foundation for a strong IT security stance. With automated patch management, secure backups, and complete visibility into your IT infrastructure, NinjaOne RMM helps you prevent ransomware attacks from the start.